The Ukrainian authorities have made several arrests and seized multiple assets in a major takedown of the Cl0p (or Clop) ransomware operation that has also seen the disruption of... Read more »
Ransomware attacks spurred close to half of all the cyber insurance claims filed in North America in the first six months of 2020, but even if a victim’s policy... Read more »
The NHS Test and Trace programme has signed UK risk management specialist Risk Ledger to proactively get to grips with cyber security risks in its supply chain, and mitigate... Read more »
The mean salary of a privacy professional has increased by approximately $6,000 (£4,260 or €4,950) in the past two years to $140,529 (£99,850 or €116,000), according to the latest... Read more »

While cyber warfare, espionage and other malicious activity backed by foreign states are pressing concerns from the perspective of an international relations specialist or foreign policy wonk, the past... Read more »

In April 2021, as organisations around the world reeled from the impact of a series of cyber attacks conducted through compromised on-premise Microsoft Exchange servers, the US Department of... Read more »

The G7 group of global economies has urged Russia and other countries that may harbour criminal ransomware groups within their borders to take accountability for tracking them down and... Read more »

Benoît Dewaele, chief information officer at Belgian food group Vandemoortele, is looking to connect with the chefs of Europe. They are key customers for the group’s range of frozen bakery goods, margarines, culinary oils and fats. From... Read more »
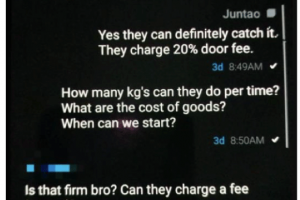
Three years ago, the FBI began planning a sophisticated sting that led to the arrests of 800 suspected organised criminals in raids around the world. Police this week carried... Read more »

The Competition and Markets Authority (CMA) has secured a number of commitments from Google on the design and development of its Privacy Sandbox proposals for the replacement of third-party... Read more »

