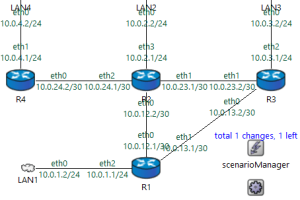
Routing protocols tell your routers how to talk to one another and then govern how each of them should distribute information. In short, it helps routers plan their routes... Read more »
Spyware is a malicious software program placed on a user’s computer without their permission. Once the spyware enters the computing environment, it gathers confidential information and transmits it to... Read more »
A Trojan horse—also called a Trojan virus or simply a Trojan—is a type of malware that disguises itself as legitimate software. They appear innocent or beneficial from the outside,... Read more »
A firewall is a security measure that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between a trusted internal... Read more »
A host-based firewall is a type of firewall specifically designed to provide security to a single host, such as a computer or server, by monitoring and controlling its incoming... Read more »
The goal of any computer virus is to infect a victim’s device with code that creates problems for the system and the user. Viruses can alter or delete files,... Read more »
Download this template as a PDF or DOC to modify it for your organization: PDF Download DOCX Download For more information, read our complete guide to setting a firewall... Read more »
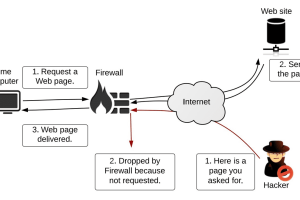
As the number of cyber attacks on organizations continues to rise, organizations must take necessary measures to protect their systems and networks. One such measure often used by organizations... Read more »

Although many enterprises are working hard to virtualize and replace their legacy network hardware, a large number of companies still rely on their on-premises tools, particularly in the realm... Read more »

An operating system (OS) is software that manages a computer’s hardware and software resources, enabling users to interact with the computer, manage systems files, install software, and execute programs.... Read more »

