The emergence of big data has opened up numerous possibilities for businesses to tap into this vast potential. Data-driven AI (artificial intelligence) and ML (machine learning) initiatives can help... Read more »
Recent data breaches have forced enterprises to question everything they know about security. The days when a firewall and software-isolated networks were kept up-to-date on individual endpoints are long... Read more »

Given the increasing rate of cyber crimes, cybersecurity professionals are in demand. Here are the best cybersecurity certifications that can help forward your career. What is a Cybersecurity Certification?... Read more »
Enterprise security often fails for a few specific reasons: misconfiguration and poor tooling, lackluster training and user errors, or a total lack of communication across teams. DevSecOps, a combination... Read more »
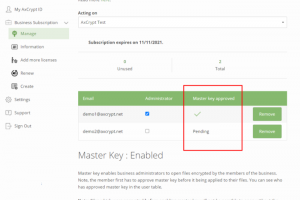
Whether it’s for something as simple as the internal sharing of a customer profile or a more complex task such as the transfer of all company files during an... Read more »
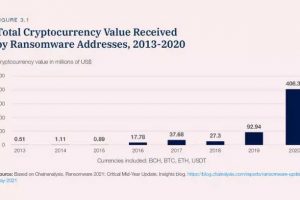
We live in an increasingly dangerous world. The internet is littered with nefarious crooks that will stop at nothing to exploit an organization’s vulnerabilities, steal data, or plant ransomware.... Read more »
To keep software up-to-date and secure, software developers roll out patches to their applications from a central server on a regular basis. Because of frequent patch releases and the... Read more »
Digital forensics tools gather evidence from digital devices for solving cyber crimes. Here is all you should know about the best digital and computer forensics tools available today. What... Read more »
A cloud outage can be a nightmare for any organization. When your critical applications and data are hosted in the cloud, an unexpected outage can bring business to a... Read more »
In light of Russia’s invasion of Ukraine, cloud service providers are tightening cybersecurity measures to protect clients who are located in and/or do business with Ukraine and other Eastern... Read more »

