As a technology standard for broadband cellular networks, it is reasonable to think of 5G as a hardware-based entity. However, much of 5G architecture and networking mechanics rely on... Read more »
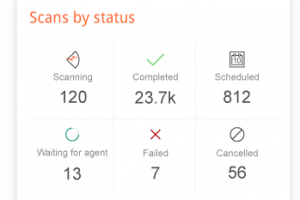
As enterprises digitally transform and continue to evolve into hybrid models of work, their networks and device ecosystems grow ever larger. This makes an enterprise’s network more difficult to... Read more »
The fifth generation of cellular technology, or 5G, has started rolling out in pockets around the globe, bringing expanded network connectivity and speed to new users and device types.... Read more »
In the B2B environment today, 80% of seller-buyer interactions will happen digitally by 2025. B2B buyers’ increasing adoption of a digital-first approach to buying makes their internet activities that... Read more »

A content delivery network (CDN) provides secure, efficient, and quick delivery of content to websites and internet services. In this guide, we will discuss the best CDN providers in... Read more »
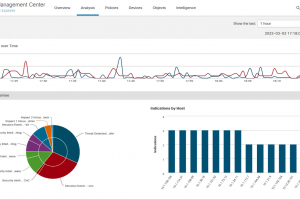
A decade ago, intrusion detection and prevention technology was regarded as a luxury for enterprises with larger budgets. Today, protection against internal and external threats is an absolute necessity.... Read more »
The business world has begun to realize the importance of robust cybersecurity. It’s the top IT spending priority for businesses in 2022, with 69% of organizations increasing their security... Read more »
The rise of development environments like Agile and DevOps means developer teams can now release application software even multiple times a day. While this has been a blessing for... Read more »
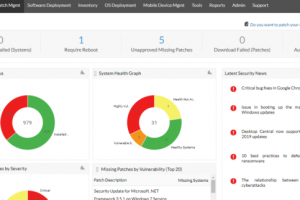
When a security vulnerability is discovered in software or network infrastructure code, it rarely makes sense to overhaul the whole product, especially due to the time, cost, and frequency... Read more »
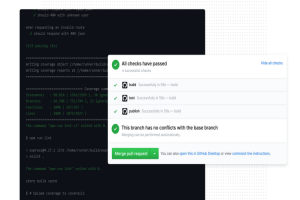
In the fast-paced software development market of today, catering to the needs of customers while efficiently competing with competitors is not easy. Organizations should employ a hardy toolkit to... Read more »

