A computer worm is a type of malware that self-replicates and spreads across a network or system without any user intervention. Unlike other forms of malware, such as viruses... Read more »

All forms of IT virtualization aim to create an abstraction layer between the physical hardware and the services and applications that use the hardware. In network virtualization, network functions,... Read more »
A rootkit is malicious software (malware) designed to gain unauthorized access to a computer system and maintain control over it while remaining hidden from the user or system administrators.... Read more »
The Open Systems Interconnect (OSI) model is a seven-layer visual model that describes the networking system and how apps can communicate with each other. In the earlier days of... Read more »

Proxmox Virtual Environment (VE) and Red Hat Virtualization are two popular virtualization solutions designed to support organizations of varying sizes. Both are solid, dependable choices for virtualized architecture with... Read more »
Botnets (derived from “robot networks”) are networks of computers or devices that have been compromised by malware and are under the control of a remote attacker (often called a... Read more »
Ransomware-as-a-service (RaaS) is a pay-for-use subscription model on the dark web where developers license out malware to other parties to execute targeted ransomware attacks. RaaS is advertised on the... Read more »
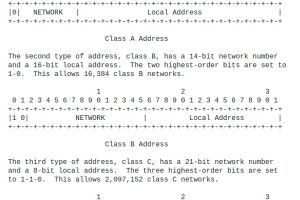
Classless Inter-Domain Routing (CIDR) is an IP addressing system that replaced the previous system of using Class A, B, and C networks. CIDR was developed to help alleviate the... Read more »
Network routing is the decision-making process for routers as they learn available routes, build tables, and send data on the fastest and cheapest paths. These tasks optimize efficiency and... Read more »
Multicast routing is a protocol that sends one copy of data to multiple users simultaneously on a closed network. The most popular uses of multicasting include videoconferencing and streaming... Read more »

