People often argue it’s impossible to prepare for or fight back against threats without knowing what they are. That understanding highlights the need for thorough and regularly performed network audits. The vulnerabilities found in these examinations are sometimes the first aspects hackers try to exploit in their attacks.
What is a network audit?
A network audit is a formal or informal inventory, assessment, and analysis of your network’s hardware, software, operating systems, servers, and users.
Network audits typically check:
- All network infrastructure and internet-accessible systems
- The security mechanisms activated to protect the network
- The practices used for day-to-day network management
This guide will walk you through the eight essential steps to perform a network audit at your organization.
What should be included in a network audit checklist?
Careful planning of a network audit is essential for ensuring people don’t overlook valuable and necessary steps. From selecting your tools and personnel to preparing the post-audit report, here’s a breakdown of each element.
1. Decide on the necessary tools or personnel
Company representatives should begin by discussing whether they need to invest in specialized tools or hire network security experts such as a managed service provider (MSP) before starting the audit. Trying to do the necessary checks without the proper resources could make everything take longer than it should.
Organizations who need to hire help before starting an audit should be aware that the process may take longer than anticipated. A 2022 Gartner study of audit leaders found their top challenge was recruiting auditing professionals with non-traditional skills, with 57% of respondents mentioning that obstacle.
2. Verify the existing network security policy
Every business should have an in-depth network security policy that applies to all employees, guests, service providers, and other entities that do or could use the network. Looking at that document before and during the network is an excellent way to spot evidence of non-compliance or room for improvement.
You’ll also want to consider what’s changed within the organization since the most recent network security update and what’s on the horizon. The current document may not be as relevant as it could be. Now is a great time to bring it up to speed.
3. Settle on the audit’s scope
All those involved in the audit must agree on what it covers. What companies ultimately decide in this regard often depends on their time frames and budget. During this step, you should also take a network inventory to become more familiar with total assets.
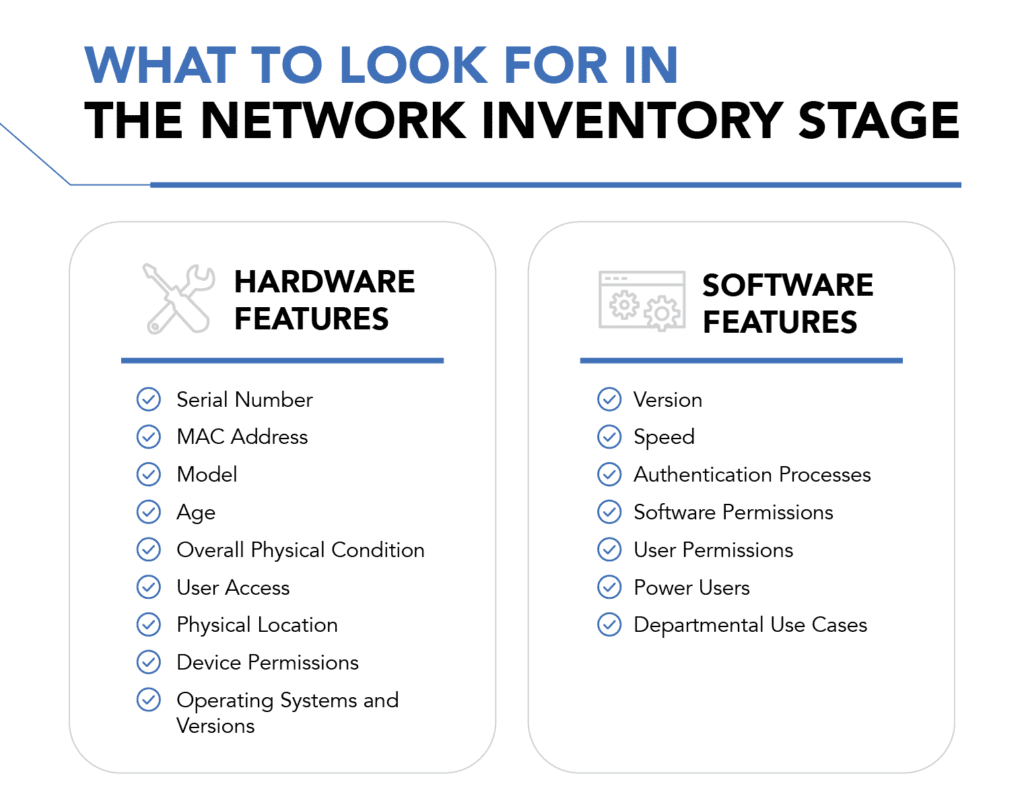
Some network audits only extend to network devices, such as routers and firewalls. However, many often include an organization’s servers and computers as well. A particularly thorough audit even covers the network’s applications. Your plan should be clear about what the audit does and does not encompass.
4. Understand which threats to look for
Getting ready for a network audit means knowing the cyber threats most likely to disable the infrastructure. For example, a 2022 study from Titania found exploitable network misconfigurations cost at least 9% of a business’s annual revenue. Another surprising takeaway was that people only check routers and switches in 4% of security audits, even though doing so can significantly reduce the attack surface.
Elsewhere, a 2023 report of risk professionals found 50% were most concerned about an increase in ransomware attacks. Network audits should always proceed with an awareness of which threats specific networks face. Security teams can then ensure the infrastructure has the necessary safeguards against them.
5. Target what’s not working well
Improving network security involves understanding when specific procedures, practices, or safeguards don’t work as well as they could. Do network security team members often mention processes that are time-consuming or prone to error? If so, the network security audit may identify tasks that are excellent automation candidates.
Also look for any gaps in security coverage. Do additional people, software, or systems have unaccounted for or risky permissions? Does some software have weak or nonexistent authentication processes? Are certain systems so out-of-date that they are not operating as expected in your security policy?
Mapping out these shortcomings will help you determine how everything is connected and where some of your network’s weaknesses lie.
6. Review how network access happens
A network security audit poses a fantastic opportunity to review what authorized users do to access the network. Those details can sometimes reveal weaknesses, too. Perhaps the IT team was previously not overly concerned with how much network access each employee had. But changing permissions so each staff member only has what they need limits the damage a hacker could cause after stealing someone’s credentials.
The security audit should also check the procedures for letting guests use the network. Some companies segment guest access. That way, if things go wrong, such users can only access small parts of the overall network.
7. Perform a penetration test
A penetration test—or pen test—is when a security expert examines the network as a hacker would, looking for vulnerabilities and ways to exploit them. It’s best if the pen tester has little or no prior knowledge of how a company secures its network. Then, the information they have at the start of the exercise is as close as possible to a hacker’s.
Penetration tests can have various goals. For example, the tester may perform them from within the company, taking the position of a disgruntled employee. In other cases, everything happens off the organization’s property, with the pen tester working remotely.
The pen test is a helpful part of a network audit because it gives insight into what hackers could do if given the opportunity. That helps IT be more targeted and proactive and fix those weaknesses before a real-life hack occurs.
8. Prepare the post-audit report
The post-audit report is a detailed breakdown of all the examination’s findings. It explains what an organization is doing well and its network security weaknesses. These reports often contain diagrams and charts, making the content easier to understand and act on.
Anyone involved in making or reviewing the report must keep the intended audience in mind. Perhaps most people who will read it are C-suite members without extensive tech backgrounds. In that case, the document must have accessible language and tie cybersecurity to overarching business goals. It’s also critical to include action items in this final report so that stakeholders can create a plan of action to address any necessary changes.
Who is usually involved in a network audit?
In larger enterprises where IT resources and expertise abound, your internal IT or auditing team can complete an internal network audit under the direction of a network analyst and information systems auditor. But for smaller companies or companies that want an unbiased outside perspective, an MSP can conduct the audit and deliver the results to your team.
Once you have your auditor or auditing team in place, they will need widespread access to all nodes within the network, so that they can manually assess or use a network auditing tool to assess the network. Assessment is not the only key phase in the process; it is also important for your auditing team to present the results to stakeholders such as C-suite and for internal teams to make the necessary changes to your network.
If a company is doing a network audit as part of a cyberattack recovery, the parties who investigated that event and found the cause will often be part of the network audit, too. That’s especially true if the cyberattack happened because of a network-related vulnerability.
When should you conduct a network audit?
Organizations of any size and industry should complete network audits on a regular basis—at least annually. Regular audits can help your IT team and your leadership team to keep up with your network’s needs and threats as your enterprise and its daily operations change over time.
How network audits affect your cybersecurity
Cybersecurity strategies must have three parts to work effectively: prevention, detection, and remediation. A network security audit covers the first two prongs by giving representatives the knowledge necessary to stop attacks and become aware of which vulnerabilities hackers will target and take advantage of during future attacks.
Security providers can only protect businesses against threats if they know the existing problems. Network audits provide that valuable information, allowing organizations to become proactive rather than reactive in handling cybersecurity. Successful attacks have the potential to become far too damaging for organizations to do anything other than continually look for vulnerabilities and fix them before hackers can exploit those issues.
Bottom line: Creating a network audit checklist
Being thorough with a network audit is one of the best ways to protect against dangerous, damaging, and expensive cyberattacks. An effective network audit checklist will help teams who are doing these cybersecurity examinations for the first time as well as those who have scrutinized their networks before but want to be sure they cover all their bases. Wherever your organization stands in its current security posture, it must consider network audits as essential for keeping its networks and data safe.
The right partners and solutions can take some of the challenge and guesswork out of securing your network. Here are the top network security companies to consider working with.
The post Network Security Audit Checklist: 8 Essential Components appeared first on Enterprise Networking Planet.

