We live in an increasingly dangerous world. The internet is littered with nefarious crooks that will stop at nothing to exploit an organization’s vulnerabilities, steal data, or plant ransomware. Moreover, the threat actors are no longer sole individuals working from basements—sophisticated criminal networks and foreign governments now perpetrate attacks.
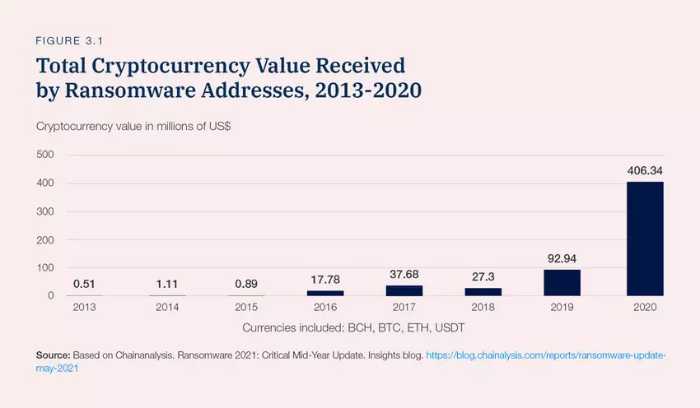
Nothing demonstrates the severity of the problem better than the Global Risks Report 2022 published by the World Economic Forum. According to the study, the total value of cryptocurrency received by ransomware addresses has grown steadily from 2013 to hit a high of $406.34 million in 2020. If you doubt the utility of vulnerability management tools and software, that statistic should dispel them.
Why is Vulnerability Management Required?
The first step in understanding why vulnerability management is required is to understand the different types of attacks that attackers can launch against an organization. The most common types of attacks are:
- Malware: Malicious software designed to damage or disable computers and computer systems.
- Ransomware: A type of malware that encrypts data on a victim’s computer and then demands a ransom payment to unlock it.
- Phishing: A scam in which criminals trick targets into giving personal information, such as passwords or financial data. Original phishing scams were conducted over email, but today there are various other communication channels attackers use, such as social media and text messages. Messages appear to be from reputable organizations or people.
- Insider Threat: A malicious or unauthorized act by an employee or contractor that can jeopardize the security of an organization’s IT assets.
- Web Application Attacks: Attacks against web applications that can include SQL injection attacks, cross-site scripting (XSS), and session hijacking.
- Social engineering: The use of deception to manipulate individuals into divulging confidential information.
- DDoS attacks: Distributed denial of service attacks use multiple computers to flood a target with traffic, making it impossible for the target to respond to legitimate requests.
Organizations can be vulnerable to a wide variety of attacks, and the list above is just a sampling. Vulnerability management is essential because it helps organizations protect themselves from these attacks by identifying and patching vulnerabilities in their networks before the threat actors can exploit them.
Also read: Best Unified Endpoint Management (UEM) Software 2022
What are Vulnerability Management Tools?
There are a variety of vulnerability management tools and software available on the market, but the most common ones fall into the following five categories:
- Attack Surface Management Software: Attack surface management software helps organizations visualize and manage the attack surface of their networks. The attack surface is the sum total of all points where an attacker could potentially launch an attack against an organization. These include networks, cloud services, and other IT assets. Attack surface management software helps organizations identify and close any gaps in their security posture. They also automate numerous tasks such as real-time vulnerability scanning and threat analysis, which helps to reduce the time and effort required to maintain a secure network.
- Patch Management Software: Patch management software is used to deploy and manage patches for operating systems, applications, and firmware. It allows organizations to automate the patching process, a time-consuming and labor-intensive task. Patch management software also provides reporting and analytics so organizations can track the progress of their patching efforts and ensure that they address all vulnerabilities.
- Risk-Based Vulnerability Management Software: Risk-based vulnerability management software uses machine learning algorithms to prioritize vulnerabilities based on their likelihood and impact. This approach helps organizations focus their resources on the most critical vulnerabilities first. Risk-based vulnerability management software also provides detailed reports on an organization’s security posture, which can help with risk assessment and risk management.
- Secure Code Training Software: Secure code training software helps organizations create and enforce a secure coding standard across their development teams. This helps ensure that all code is written securely and reduces the likelihood of vulnerabilities being introduced into the codebase. Secure code training software also provides automated testing and reporting, which helps identify coding errors and vulnerabilities early in the development process.
- Security Awareness Training Software: Security awareness training software helps organizations assess their employees’ security awareness and knowledge. Businesses use these solutions to outsource security training to specialists with experience and courses covering a range of security tactics. In addition, many of these programs provide simulated attacks to assist workers in distinguishing malicious content before they see it in real life.
Also read: Patch Management Trends for 2022
5 Best Vulnerability Management Tools
Many different tools and software programs can help businesses with vulnerability management. Below, we will look at some of the top vulnerability management tools and software programs available on the market today for each of our five categories above.
Detectify Best | Best Attack Surface Management Software
Detectify is a fully automated Attack Surface Management software that leverages a global ethical hacking community. Security teams use Detectify to map out the entire attack surface, identify anomalies, and detect new business-critical vulnerabilities in time—especially in third-party software—utilizing hacker insights. Hacking your attack surface is the best way to secure it, and Detectify makes this possible with a few short clicks.
Key Features
- Surface monitoring: If you have multiple assets to consider, Detectify makes it easy to scan your servers and what you host with Surface Monitoring. You can easily keep track of a large number of internet-facing assets, discover misconfigurations and vulnerabilities, as well as find instructions on how to fix them across your entire attack surface.
- Application scanning: Detectify’s scanning engine crawls through your web applications and websites, looking for vulnerabilities. It detects everything from XSS and SQLi to broken authentication and session management. The scanner is updated daily with new vulnerabilities from the Detectify community and commercial bug bounty programs.
- Crowdsource ethical hackers: The Detectify community consists of thousands of white-hat hackers who are constantly finding new vulnerabilities and helping to make the internet a safer place. When you join Detectify, you get access to this global community of security experts who can help you find and fix vulnerabilities in your applications and websites.
- Empowers security defenders: With the proper knowledge, every member of your organization, from security teams and developers to department managers, can do their part to make sure your public-facing IT assets are as secure as possible. Detectify makes it easy for anyone to participate in your security by providing clear and concise vulnerability reports, recommendations, and fix instructions.
Pros
- Simple to use
- Good insights into emerging and existing vulnerabilities
- A global community of ethical hackers
- Few false positives
Cons
- Some deep scans take very long
Pricing
Detectify has two products priced as follows:
- Surface Monitoring costs $289 per month (billed annually) per apex domain (up to 25 subdomains).
- Application Scanning costs $85 per month (billed annually) per scan profile.
Microsoft System Center | Best Patch Management Software
We chose Microsoft System Center as the best patch management software because numerous organizations use Microsoft products. The software behemoth remains the number one desktop operating system provider with a 74% market share, and its cloud platform Azure is second behind AWS with a market share of 21%.
System Center is the key to managing, deploying, and monitoring updates for Microsoft software in your organization. In addition, it can help increase your security posture by automating the process of patch management and ensuring that your software is always up to date.
System Center can be used to manage updates for the following products:
- Windows 10
- Windows Server 2016
- Office 365
System Center also integrates with other Microsoft products such as Azure and Intune, making it an even more valuable tool for organizations looking to manage their Microsoft software estate.
Key Features
- Automatic updates: System Center can be configured to download and install updates for Microsoft products automatically. This ensures that your software is always up to date and reduces the risk of vulnerability exploits.
- Patch management: System Center enables you to patch your Microsoft software both on-premises and in the cloud. You can configure it to patch as many or as few systems as you want, and you have the option to patch immediately or schedule patches for a later time.
- Compliance: One of System Center’s key features is its ability to help organizations maintain compliance with industry regulations such as HIPAA and PCI-DSS. It can do this by automating the patch management process and ensuring that all systems are updated and compliant.
- Endpoint protection: System Center also includes endpoint protection, a suite of security software that helps protect your organization’s computers from malware and other malicious threats, unauthorized access to data, and restricts access to specific applications and websites.
Pros
- Integrates with other Microsoft products
- Can automate the patch management process
- Helps organizations maintain compliance.
- Faster time-to-value
- Support for heterogeneous environments. For example, you can manage and monitor Windows Server, Hyper-V, VMware, and Linux.
Cons
- Requires significant expertise to plan and set up
Pricing
Microsoft System Center is available in two editions:
- Standard Edition for managing physical servers: A two-year price of $1,323 licensed by cores.
- Datacenter Edition for managing virtual servers: A two-year price of $3,607 licensed by cores.
Tenable.sc | Best Risk-Based Vulnerability Management Software
Legacy vulnerability management solutions were not built to handle today’s attack surface and the increased number of threats that come with it. Instead, they are restricted to a theoretical risk assessment, resulting in security teams spending the majority of their time chasing after wrong issues while missing the most severe vulnerabilities that pose the highest risk to the organization.
Taking a risk-based approach to vulnerability management, Tenable.sc allows security teams to focus on the vulnerabilities and assets that are most important to their organization’s real business risk, rather than wasting time on vulnerabilities with a low probability of exploitation. This approach allows you to prioritize remediation and reduce risk with the least effort and human resources.
Key Features
- Active scanning: Active scanning, CMDB connections, passive monitoring, and agents provide a comprehensive and continuous picture of all of your assets, including those that were previously undetected.
- Extensive CVE coverage and security configuration: With coverage for over 66,000 vulnerabilities, the Tenable.sc vulnerability database provides extensive Common Vulnerabilities and Exposures (CVE) coverage.
- Predictive prioritization: The Tenable.sc platform includes a patented engine that provides predictive prioritization of vulnerabilities, so you know which ones pose the greatest risk to your organization.
- Free API access for customer integrations: The Tenable.sc platform offers free REST API access, making it easy to integrate your existing tools and processes.
Pros
- Flexibility in data control
- The dashboard is intuitive and offers a great user experience
- Vulnerability priority rating
- Good out-of-box integration
- Excellent customer support
Cons
- Documentation needs improvement
Pricing
Clients pay an annual subscription priced by IP. There is also the option of a perpetual license. In addition, the company offers a 30-day free trial.
Immersive Labs | Best Secure Code Training Software
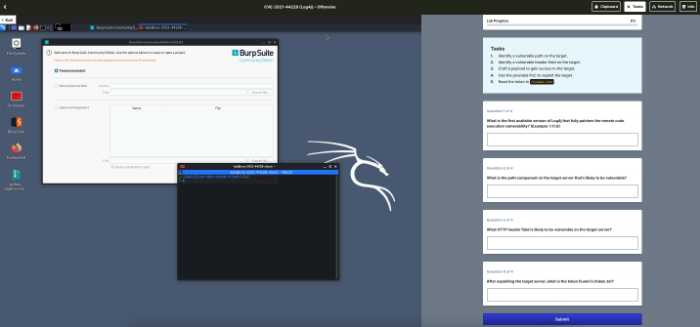
Immersive Labs allows you to demonstrate your cyber preparedness, risk, and resilience across technical and non-technical teams. The solution lets you monitor real-time cyber effectiveness in terms of cyber teams, developers, engineers, and executives all in one place fast.
The unique approach to human cyber preparedness used by Immersive Labs takes you beyond conventional training courses and certifications to engaging skills content that is directly linked to the hazards you face.
Immersive Labs is used by large high-risk organizations such as CitiBank, HSBC, and the UK’s National Crime Agency to build cybersecurity resilience.
Key Features
- Challenge-based secure coding exercises: Immersive Labs offers coding challenges designed to be realistic, relevant, and engaging.
- Realistic, role-specific, cyber simulations: The solution provides simulations tailored to your specific environment and role.
- Real-time evidence of cyber capabilities: You can see how well your team is doing in real time with clear proof of your cyber capabilities.
- Scalable content experiences: The solution grows with you, so you can add new users, content, and challenges as your needs change.
Pros
- Real-world relevance
- Hands-on exposure to vulnerability tools and cybersecurity concepts
- Challenges are fun and engaging
- Good content scalability
- Very good for team building
Cons
- Not everyone learns in the same way. Users sometimes find themselves stuck in labs for hours. A “hint” button would be a good addition.
Pricing
Immersive does not publish pricing information, but you can sign up for a free demo.
KnowBe4 | Best Security Awareness Training Software
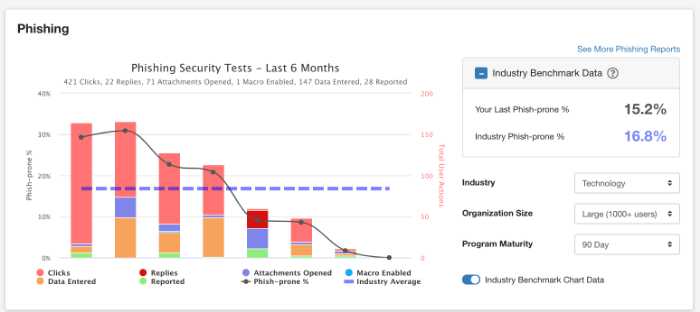
When all else fails, your users are your last line of defense. Security awareness training can help you reduce your risk of a successful attack. KnowBe4 is the world’s largest security awareness training and simulation platform, with more than 40,000 customers worldwide.
It is also the only security awareness training platform that includes content by Kevin Mitnick, a reformed hacker who was once the world’s most wanted hacker and an expert at social engineering.
Key Features
- An extensive library of security awareness training content: Lab’s library has more than 1,500 modules on various topics, including social engineering, ransomware, and hacking.
- Baseline testing: Baseline testing allows you to test your users’ knowledge before and after training. You can also track the progress of your users over time.
- Fully automated simulated phishing attacks: Labs phishing attacks are fully automated and are designed to be as realistic as possible. You can target specific users, groups, or the entire organization.
- Risk scoring: The risk scoring feature quickly assesses your risk level and prioritizes your security awareness training.
- Enterprise-strength reporting: KnowBe4 provides detailed reports that can help you track the progress of your security awareness program.
Pros
- Suitable for organizations of all sizes
- Intuitive and user-friendly
- Good tech support with short response times
- Unlimited access to phishing features
- Flexible pricing
Cons
- There is a considerable disparity in the amount of training available between the top two pricing plans.
Pricing
There are four pricing tiers. Subscriptions are priced per seat annually with generous discounts for a three-year contract. The complete pricing list is as follows:
| Pricing By Seat per 1 Year | Silver | Gold | Platinum | Diamond |
| 25-50 | $18.00 | $21.75 | $25.50 | $30.50 |
| 51-100 | $16.00 | $19.25 | $22.50 | $27.50 |
| 101-500 | $13.00 | $15.50 | $18.00 | $23.00 |
| 501-1000 | $12.00 | $14.25 | $16.50 | $21.50 |
| 1001-2000 | $11.00 | $13.00 | $15.00 | $20.00 |
| 2001-3000 | $10.00 | $11.75 | $13.50 | $18.50 |
| 3001-5000 | $9.00 | $10.50 | $12.00 | $17.00 |
| 5001+ | Get A Quote | Get A Quote | Get A Quote | Get A Quote |
Custom quotes are available for more than 5,000 seats.
How to Choose Vulnerability Management Software
One of the main takeaways from the above is that an enterprise’s approach to vulnerability management and tools should be holistic. The tools you select must cover the entire attack surface, including your weakest links: your staff. In addition, they must also be able to integrate with your existing infrastructure.
When making your decision, you should also consider the size of your organization and your budget. The five tools above are an excellent place to start to tighten up your vulnerability management program. With cybercrime on the rise, it’s more important than ever to leverage the power of vulnerability management tools and software to prevent security breaches.
Read next: Best Antivirus Software for Enterprise Security 2022
The post Top Vulnerability Management Tools & Software 2022 appeared first on Enterprise Networking Planet.

