What is Ethical Hacking?
Today’s surge in cybercrime is emboldened by constantly evolving attack vectors. The motivations behind black hat hackers and their backers pose threats ranging from those with financial motives to national security threats.
One way to keep up with these attack vectors is to authorize cybersecurity practitioners to legally bypass an organization’s security systems to expose gaps in the organization’s security posture. This is known as ethical hacking.
What are Hacking Tools?
Hacking tools can be any computer scripts, programs, or software that empower hackers to identify and exploit weaknesses in applications, systems, and networks. These are programs that penetrate application, system, or network security measures.
Ethical hacking tools are programs that are intended to allow anyone to perform security research as well as to aid security professionals in safely and legally exploiting weaknesses in digital infrastructure before threat actors do.
Also read: Top Cloud Security Posture Management (CSPM) Tools 2022
Top Hacking Tools & Software
| Tool | Vulnerability Scanning | Web Threat Management | Network Scanning | Asset Discovery |
| Intruder |  |
 |
 |
 |
| Acunetix |  |
 |
 |
 |
| Netsparker |  |
 |
 |
 |
| Metasploit |  |
 |
 |
 |
| SQLmap |  |
 |
 |
 |
| Nessus |  |
 |
 |
 |
Intruder
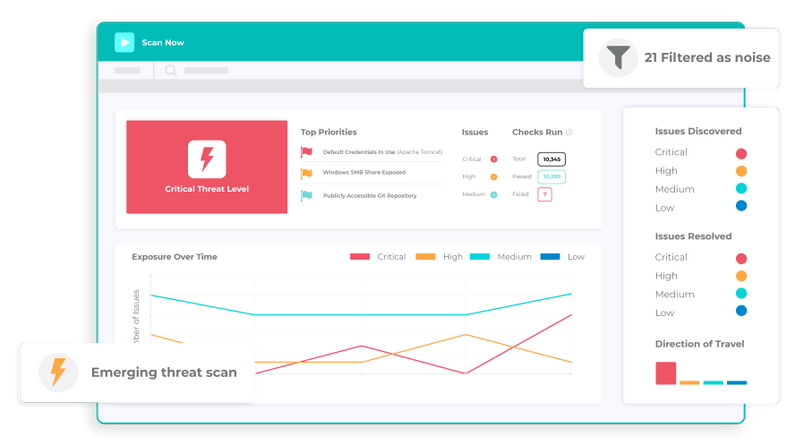
Intruder is a leading cloud-based vulnerability scanner that helps users find cybersecurity weaknesses in their online systems before threat actors do. It proactively scans for new threats and provides distinctive threat interpretation to simplify vulnerability management and avoid expensive data breaches.
Key Differentiators
- Web application testing: Intruder tests web applications and supporting services and infrastructure to ensure they are free of loopholes, vulnerabilities, and flaws.
- API penetration tests: To uncover expansive weaknesses in users’ exposed APIs, Intruder carries out API penetration tests. These weaknesses include ineffective API controls and injection attacks among others.
- Intruder Vanguard: Intruder Vanguard is a hybrid vulnerability management service that helps users continuously discover high-risk vulnerabilities under the direction of a dedicated team of certified security professionals.
- Review of cloud configurations: Intruder’s testers help users review their cloud infrastructure for misconfigured cloud systems and provide recommendations to improve or implement security best practices.
Cons: Reporting features may lack depth. Reports may also be overwhelming to non-technical users.
Pricing: Intruder offers a 30-day free trial to give users a chance to explore all of its Pro features. It has two premium plans in Essential and Pro, which are billed either monthly or annually. The Essential plan has a monthly cost of $113 and an annual cost of $1,215 while the Pro plan costs $181 monthly but $1,958 annually.
Acunetix by Invicti
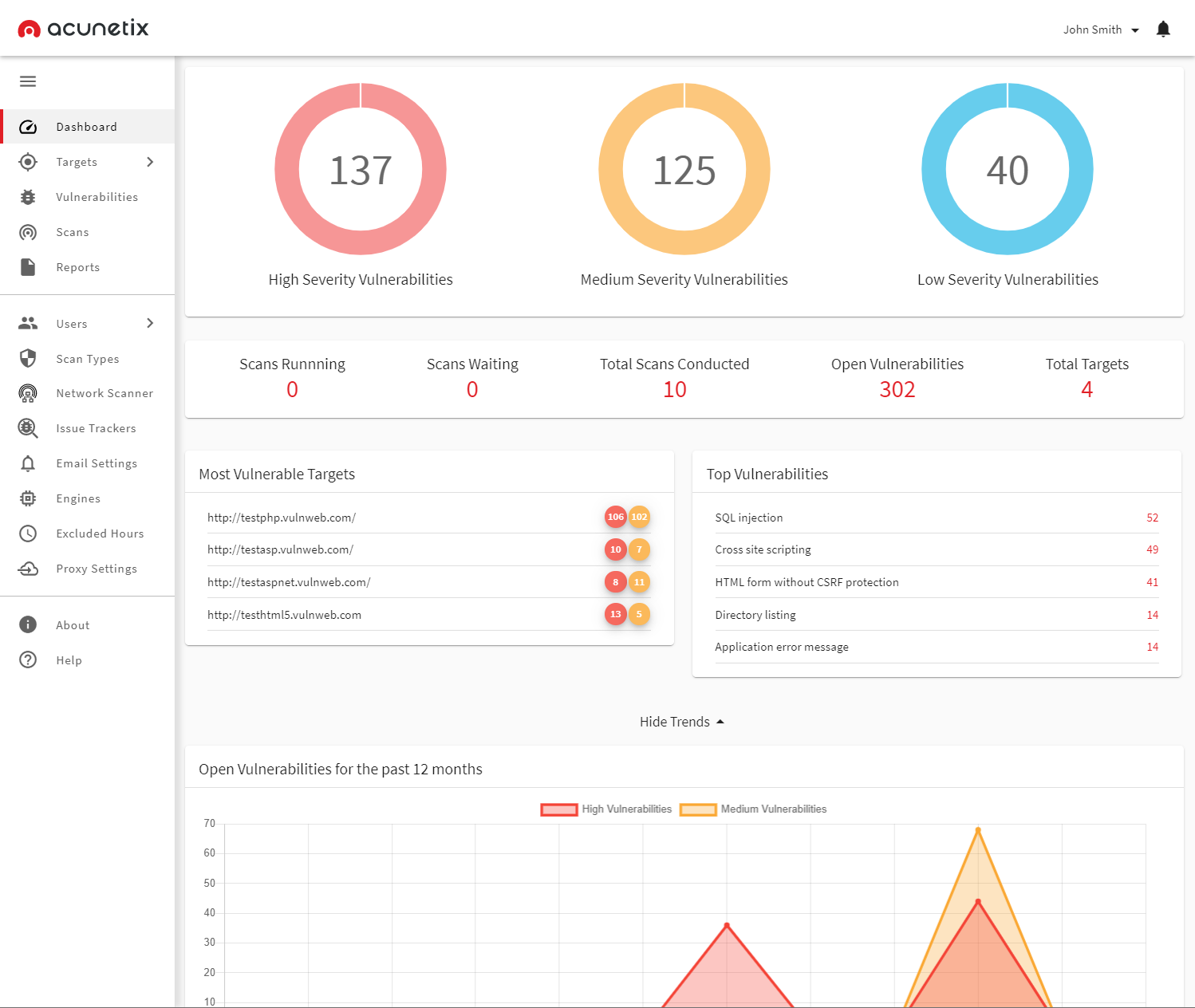
Acunetix by Invicti is an automated security testing tool that empowers smaller security teams to handle large application security problems, ensuring organizations manage risk across all kinds of web applications. It automates manual security processes and directly integrates into development tools to allow developers and security teams to work seamlessly and more efficiently.
Key Differentiators
- Third-party issue trackers: Acunetix allows the use of third-party issue trackers like GitHub, Jira, and GitLab to improve the effectiveness of vulnerability management.
- Quick and mature vulnerability scanning tools: Written in C++, Acunetix’s vulnerability scanning engine provides one of the fastest web scanning tools available to expedite scans on web applications with plenty of JavaScript code.
- SmartScan: SmartScan is a unique scanning algorithm by Acunetix that helps users uncover the majority of vulnerabilities in the first 20% of the scanning process.
- Network security scanning: Acunetix’s integration with the OpenVAS open-source tool yields a network scanner that scans users’ IP ranges to reveal open ports and network device vulnerabilities.
Cons: User interface may look dated and feel unintuitive. Scans may also take longer than expected.
Pricing: Although a demo is available, for specific pricing information you will have to contact Acunetix.
Netsparker by Invicti
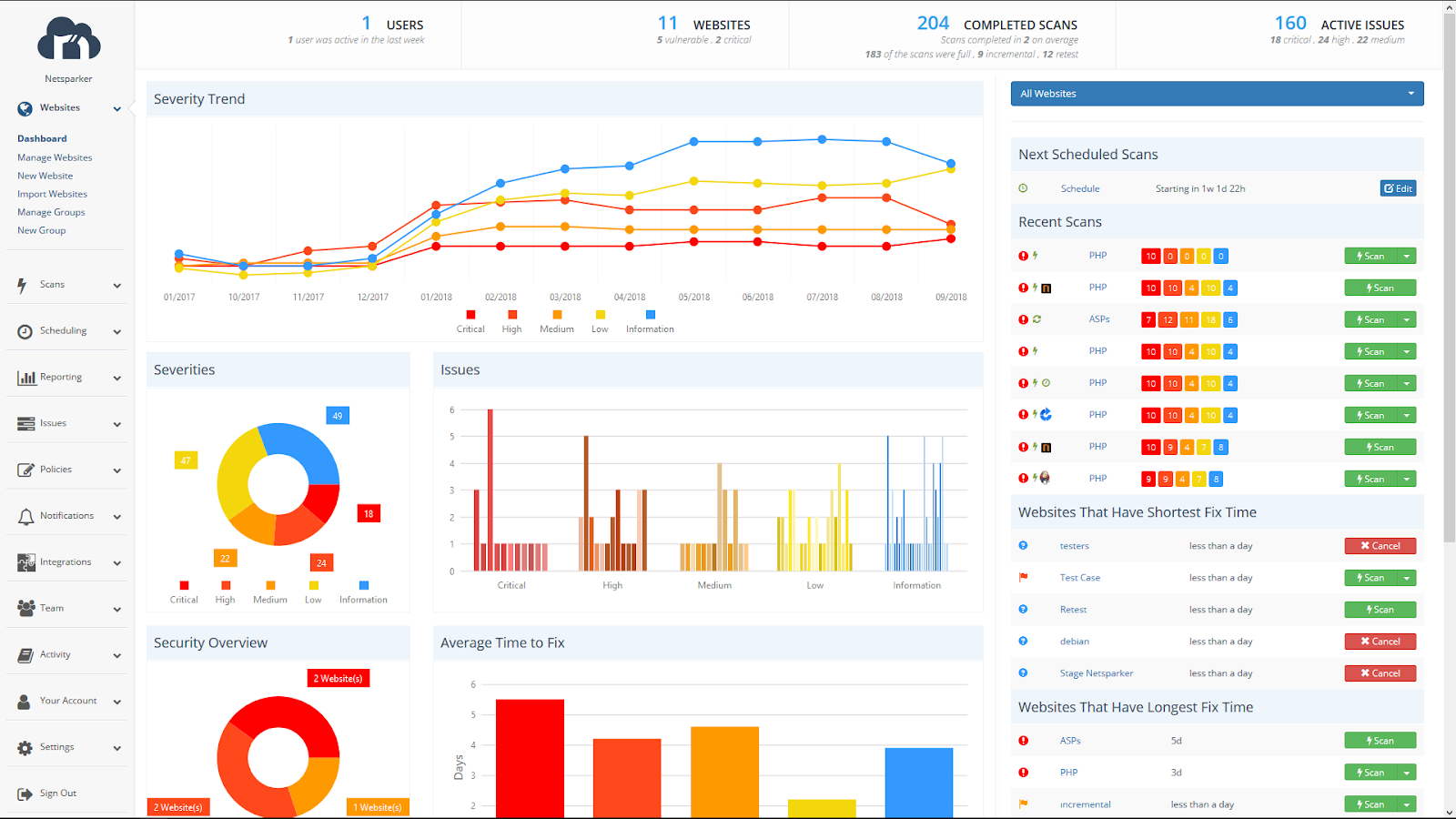
Netsparker by Invicti is an automated application security testing software that helps enterprises secure thousands of websites and greatly mitigate the risks of attacks. Enterprises with complex environments can confidently automate their web security as Netsparker provides security teams with unique scanning capabilities.
Key Differentiators
- Continuous web asset discovery engine: Netsparker continuously discovers web assets automatically to make sure the whole application attack surface is recognized and taken into consideration.
- Advanced website crawling technologies: Netsparker assures users that every inch of their applications has been checked through the use of advanced web crawling technologies to analyze all assets and uncover potential entry points for attackers.
- Industry-leading scanning accuracy: Netsparker gives users the confidence that vulnerabilities detected during scans are not false positives by automatically confirming most-direct impact vulnerabilities.
- Proof-based Scanning: To phase out manual verification and validation tasks, Netsparker pioneered Proof-based Scanning, which helps organizations confidently scale application security testing to every web asset without overrunning their security teams.
Cons: Documentation may be complex to non-security experts, and scans may become less time efficient with an increased number of items to scan.
Pricing: Netsparker offers a demo. However, for a pricing quote, you have to get in touch with Netsparker.
Metasploit
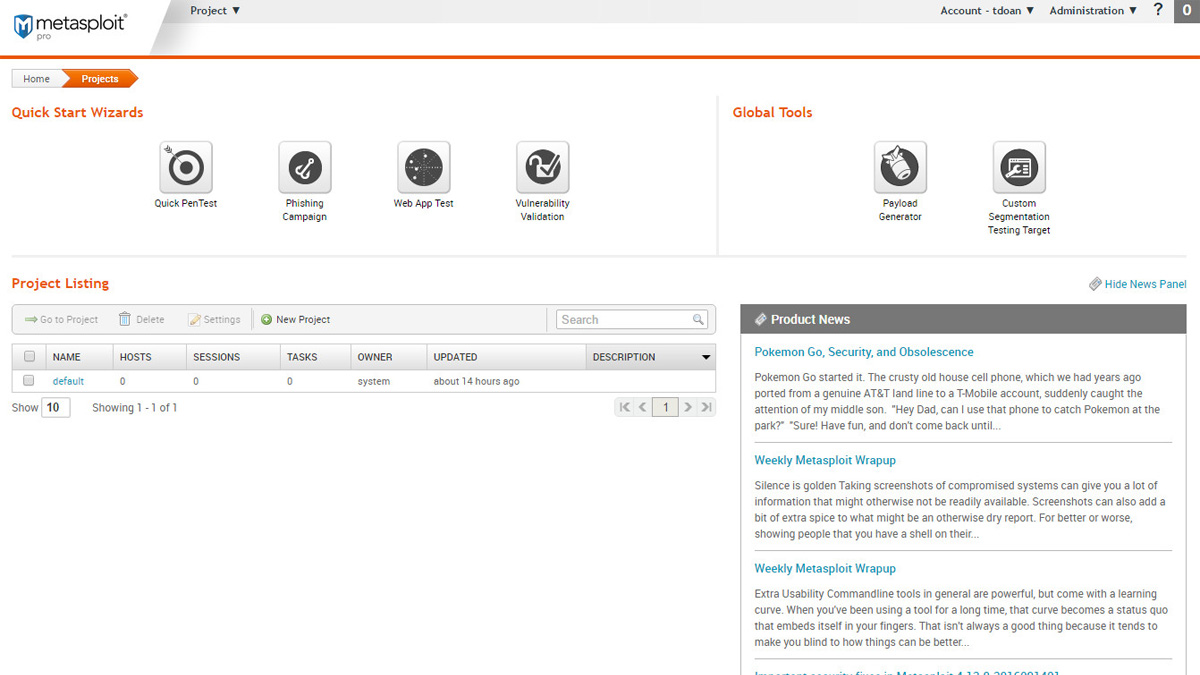
Metasploit is a penetration testing product by Rapid7 that allows users to safely simulate practical attacks on their networks to prepare their security teams to identify, mitigate, and stop real attacks. It increases the productivity of penetration testers, prioritizes and demonstrates risk, and gauges security awareness.
Key Differentiators
- Attack information: Metasploit Pro offers users access to real-world exploits through the Metasploit Framework. It automatically correlates the correct exploits upon the correct vulnerabilities and allows users to eliminate dangerous exploits to ensure the penetration test conducted at any time is safe.
- Prioritization of leading attack vectors: Users can visualize what attackers would do in an actual attack and give priority to the largest security risks through Metasploit’s simulation of complex attacks against users’ systems.
- Remediation: Metasploit tests users’ compensating controls with real attacks to ensure they are functioning correctly. The software simulates each step in the kill chain to make sure incident detection and response teams of users can catch attackers at any stage.
Cons: It could be more user-friendly, and it has a steep learning curve.
Pricing: You can download the Metasploit Framework for free. A 14-day free trial is available for Metasploit Pro, but you would have to contact Rapid7 for a quote.
SQLmap
SQLmap is an open-source penetration testing tool that offers automated detection and exploitation of SQL injection flaws and gaining control of database servers. It possesses a powerful detection engine and has a dynamic set of features and switches covering database fingerprinting, which allows users to obtain access to underlying file systems and to enforce commands on operating systems through out-of-band connections.
Key Differentiators
- DBMS support: SQLmap offers full support for numerous database management systems including MySQL, Microsoft SQL Server, PostgreSQL, Microsoft Access, Oracle, Informix, DB2, CockroachDB, MariaDB, and Sybase among others.
- Direct database connection support: With SQLmap, you can connect to a database directly using the IP address, port, DBMS credentials, and database name without going through a SQL injection.
- Dictionary-based password cracking: SQLmap automatically recognizes password hash formats and provides support for cracking these password formats through the use of a dictionary-based attack.
- Six SQL injection techniques: SQLmap provides users with full support for time-based blind, Boolean-based blind, UNION query-based, error-based, out-of-band, and stacked queries SQL injection techniques.
Con: SQLmap lacks a graphical user interface to simplify it for users who find the command-line interface to be difficult to use. Learning to use the tool has a learning curve, and there is also a lot of documentation to cover, which could become tedious.
Pricing: The software is free. However, if you seek to embed SQLmap technology into proprietary software, contact SQLmap sales to purchase alternative licenses.
Nessus
Nessus is a vulnerability assessment solution that offers users a full assessment of their environment in a rapidly changing security world. It is a solution meant to simplify vulnerability assessment and offer users peace of mind in approaching vulnerabilities, resulting in less time and effort taken to assess and remediate issues.
Key Differentiators
- Portability: Nessus gives users the flexibility to deploy on any platform regardless of how distributed their environment is or where the users are, as it is fully portable. Nessus can also be deployed on a Raspberry Pi.
- Dynamically compiled plugins: Nessus’ dynamically compiled plugins offer users increased efficiency and better scan performance, as they facilitate faster completion of initial scans as well as time to value.
- Prebuilt templates and policies: Nessus enables users to maintain best practices such as effortlessly auditing configuration compliance against CIS benchmarks. It also helps users identify where they have vulnerabilities with more than 450 preconfigured templates.
- Live Results: Live Results automatically carries out vulnerability assessments offline with each plugin update to direct users to where they may have vulnerabilities based on their scan histories.
Cons: Nessus may be a hassle to uninstall safely, as you may need to remove it piece by piece in subdirectories. It also lacks in-application remediation tracking and may generate a large number of false positives.
Pricing: Nessus Pro offers a seven-day free trial. To buy Nessus Pro, there are three licenses available. A single-year license costs $2,990 and $3,390 with advanced support. A two-year license costs $5,830 and $6,630 with advanced support. A three-year license costs $8,250. Additionally, you can contact Nessus for a custom quote.
Choosing Ethical Hacking Software
To identify the tool that is perfect for you, it is important to consider a few factors. You need to be aware of the scope of your infrastructure. For instance, Is your infrastructure solely web-based? Are your network and computer security also in consideration? By asking these questions, you will gain a better understanding of your needs and the type of tool that satisfies them. To narrow it down even further, you should consider the platforms supported by the tools in consideration.
The size of your organization and budget should also influence your decision. You need to be sure the selected tool will be well-suited to the size of your digital environment and whether you can cut costs by using open-source tools for some features that address your security needs. Finally, always consider demos where available to give you a real feel of how the tools work.
Read next: Managing Security Across MultiCloud Environments
The post Best Hacking Tools 2022: Ethical Hacking Software appeared first on Enterprise Networking Planet.

